Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
On the journey to becoming a certified Kubernetes professional, the ETCD emerges as a critical component that every CKA exam candidate must thoroughly understand. In this article, I’ll explain more about the ETCD cluster Kubernetes, provide valuable insights, aim to achieve the CKA certification, go through some topics I’m using in my studies, and revise for this exam.
Kubernetes ETCD is much more than a data storage component in the Kubernetes ecosystem. It represents the distributed and reliable brain that maintains the consistent state of the entire cluster. Mastering its concepts is not just a requirement for the exam but an essential skill for anyone working with cloud-native infrastructure.
Topics
ETCD is a distributed key-value database that stores all the information about the state of the Kubernetes cluster, and is simple, secure and fast. Developed by CoreOS, the ETCD plays a key role in managing the metadata and state of the Kubernetes cluster. It is responsible for:
To put it simply, imagine the ETCD as the “brain” of the Kubernetes cluster. Without it, Kubernetes would have no way of knowing what to run or how to react to changes. That’s why understanding how it works is essential, especially in the CKA exam, which requires practical knowledge.
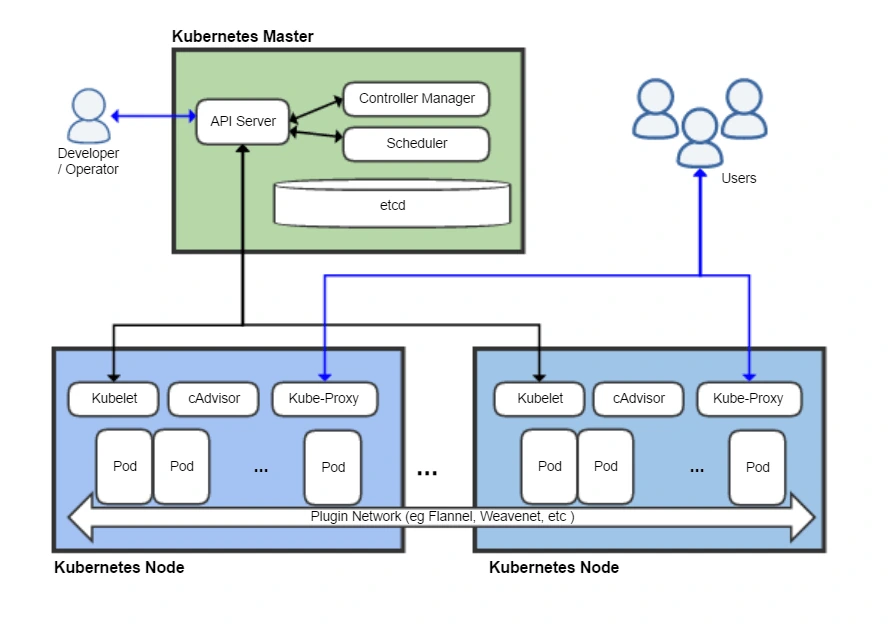
The ETCD is made up of three main components:
kubectl get command is obtained from the ETCD Server.2379, as we can see from the ETCD Pod configuration: --advertise-client-urls https://${INTERNAL_IP}:2379We can also check by looking at the running process, as shown in the image below:

ETCD uses a simple but powerful key-value storage model. Each entry is stored as a key-value pair, allowing for fast and efficient retrievals.
Example of key-value storage:
{
"name": "John,"age": 45,
"location": "New York",
"salary": 5000
}The RAFT protocol guarantees distributed consistency and is essential for the election of leaders and the replication of data between multiple nodes.
ETCD uses the Raft algorithm to ensure that all nodes have the same view of the data. It’s as if each node voted to keep the information consistent.
Download the latest version of ETCD using the curl command:
# Check the latest version at https://github.com/etcd-io/etcd/releases
VERSION="v3.5.9"
ARCH="amd64"
DOWNLOAD_URL="https://github.com/etcd-io/etcd/releases/download/${VERSION}/etcd-${VERSION}-linux-${ARCH}.tar.gz"
curl -L ${DOWNLOAD_URL} -o etcd-${VERSION}-linux-${ARCH}.tar.gzUse the tar command to extract the compressed file:
tar xzvf etcd-${VERSION}-linux-${ARCH}.tar.gz
cd etcd-${VERSION}-linux-${ARCH}/Copy the binaries to a directory in PATH:
sudo cp etcd etcdctl /usr/local/bin/For security purposes, create a dedicated user for the ETCD service:
sudo useradd --no-create-home --shell /bin/false etcdsudo mkdir -p /etc/etcd /var/lib/etcd
sudo chown -R etcd:etcd /var/lib/etcdCreate a systemd service file:
sudo vi /etc/systemd/system/etcd.servicePaste the following content:
[Unit]
Description=etcd key-value store
Documentation=https://github.com/etcd-io/etcd
After=network.target
[Service]
User=etcd
Type=notify
ExecStart=/usr/local/bin/etcd \
--name etcd-server \
--data-dir /var/lib/etcd \
--listen-client-urls http://localhost:2379 \
--advertise-client-urls http://localhost:2379
Restart=always
RestartSec=5
LimitNOFILE=65536
[Install]
WantedBy=multi-user.targetsudo systemctl daemon-reload
sudo systemctl enable etcd
sudo systemctl start etcdsudo systemctl status etcdVerify if the ETCD is working properly:
etcdctl version
etcdctl put myKey "Test Value"
etcdctl get myKeyAdvanced settings
For more complex configurations, such as distributed clusters, consult the official ETCD documentation.
One of the areas where etcd is most explored in the CKA exam is in the troubleshooting part. You may be asked to identify problems in etcd or even restore a backup. Here are some important topics to review:
etcdctl snapshot saveDuring the exam, you will need to perform tasks in the ETCD. Here are some of the most important commands:
# Check ETCD status
ETCDCTL_API=3 etcdctl endpoint status --write-out=table \
--cacert=/etc/kubernetes/pki/etcd/ca.crt \
--cert=/etc/kubernetes/pki/etcd/server.crt \
--key=/etc/kubernetes/pki/etcd/server.key
# Back up ETCD
ETCDCTL_API=3 etcdctl snapshot save snapshot.db \
--cacert=/etc/kubernetes/pki/etcd/ca.crt \
--cert=/etc/kubernetes/pki/etcd/server.crt \
--key=/etc/kubernetes/pki/etcd/server.key
# Restore ETCD from a backup
ETCDCTL_API=3 etcdctl snapshot restore snapshot.db \
--data-dir=/var/lib/etcd-restored
# General etcdctl commands
etcdctl snapshot save
etcdctl endpoint health
etcdctl get
etcdctl putexport ETCDCTL_API=3 variable, as some commands may not work between versions.--cacert /etc/kubernetes/pki/etcd/ca.crt
--cert /etc/kubernetes/pki/etcd/server.crt
--key /etc/kubernetes/pki/etcd/server.keyN/2 + 1, where N represents the total number of nodes. See how this impacts different cluster configurations:1 Node:
2 Nodes:
3 Nodes:
4 Nodes:
5 Nodes:
To backup and restore ETCD in Kubernetes, the 2 main commands involved are these:
# Back up
ETCDCTL_API=3 etcdctl snapshot save snapshot.db
# Restore the snapshot
ETCDCTL_API=3 etcdctl snapshot restore snapshot.dbHowever, when carrying out the procedures there are other important commands and a few more details, which I’ll go into in detail in the steps below.
Before you start, make sure:
etcdctl installed# Set ETCD API version
export ETCDCTL_API=3
# Basic backup command
etcdctl snapshot save snapshot.db
# Backup with authentication parameters
etcdctl snapshot save /tmp/snapshot.db \
--endpoints=https://127.0.0.1:2379 \
--cacert=/etc/kubernetes/pki/etcd/ca.crt \
--cert=/etc/kubernetes/pki/etcd/etcd-server.crt \
--key=/etc/kubernetes/pki/etcd/etcd-server.keyFirst of all, you need to understand the parameters used in the save command:
--endpoints: The address of the etcd endpoint (usually https://127.0.0.1:2379 in local clusters).--cacert: Path to the certificate of the Certificate Authority (CA) that validates the SSL/TLS communication.Normally, etcd is configured in the file /etc/kubernetes/manifests/etcd.yaml, which defines the static Pod for etcd. Use the command below to check:
cat /etc/kubernetes/manifests/etcd.yamlSearch for something like:
- --listen-client-urls=https://127.0.0.1:2379The value will be the etcd endpoint. In most cases, this is https://127.0.0.1:2379.
Certificates are usually generated by kubeadm and can be found at:
ls /etc/kubernetes/pki/etcd/You will see files like:
ca.crt (CA of etcd)server.crt (Server certificate)server.key (Server’s private key)These paths are used for the --cacert, --cert and --key parameters:
--cacert=/etc/kubernetes/pki/etcd/ca.crt
--cert=/etc/kubernetes/pki/etcd/server.crt
--key=/etc/kubernetes/pki/etcd/server.keyetcdctl snapshot status snapshot.dbStep-by-step Restoration:
service kube-apiserver stopetcdctl snapshot restore snapshot.db \
--data-dir /var/lib/etcd-backupsystemctl daemon-reloadservice etcd restartservice kube-apiserver startComparing ETCD with the main storage solutions:
| Feature | ETCD | Consul | ZooKeeper |
|---|---|---|---|
| Consistency | Strong | Strong | Eventual |
| Performance | High | Average | Average |
| Scalability | High | Average | Low |
The ETCD stores the complete state of the cluster, configurations and metadata, and is essential for the stability and recovery of the environment.
Use TLS, configure certificates correctly and limit access to authorized components only.
Periodic backups are recommended, preferably with each significant change in the cluster.
Learning more about ETCD is not just a requirement for the CKA exam, but a fundamental skill for professionals who are going to work with Kubernetes. Spend time practicing, exploring its architecture and understanding its internal mechanisms, carrying out simulations and tests in the lab, before getting hands-on in production or applying your knowledge in the CKA exam.
📚 Explore more content about Kubernetes.
🚀 See how to install Kubeadm on WSL2 to help with labs and studying for the CKA.
Good luck with your CKA exam! 💪